About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 1190 results for "Ian M Hamilton" clear search
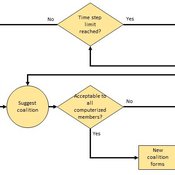
Heuristic Algorithm for Generating Strategic Coalition Structures
Andrew Collins Daniele Vernon-Bido | Published Monday, October 12, 2020The purpose of the model is to generate coalition structures of different glove games, using a specially designed algorithm. The coalition structures can be are later analyzed by comparing them to core partitions of the game used. Core partitions are coalition structures where no subset of players has an incentive to form a new coalition.
The algorithm used in this model is an advancement of the algorithm found in Collins & Frydenlund (2018). It was used used to generate the results in Vernon-Bido & Collins (2021).
Peer reviewed Axelrod_Cultural_Dissemination
Arezky Hernández | Published Wednesday, March 27, 2013 | Last modified Sunday, May 05, 2013The Axelrod’s model of cultural dissemination is an agent-model designed to investigate the dissemination of culture among interacting agents on a society.
Resource distribution effects on optimal foraging theory
Marco Janssen Kim Hill | Published Friday, January 27, 2017The original Ache model is used to explore different distributions of resources on the landscape and it’s effect on optimal strategies of the camps on hunting and camp movement.
COVID-19 SIR with Public Health Interventions
Kit Martin Amber Cesare Matthew Johnson | Published Tuesday, September 28, 2021This is an extension of the basic Suceptible, Infected, Recovered (SIR) model. This model explores the spread of disease in two spaces, one a treatment, and one a control. Through the modeling options, one can explore how changing assumptions about the number of susceptible people, starting number of infected people, the disease’s infection probability, and average duration impacts the outcome. In addition, this version allows users to explore how public health interventions like social distancing, masking, and isolation can affect the number of people infected. The model shows that the interactions of agents, and the interventions can drastically affect the results of the model.
We used the model in our course about COVID-19: https://www.csats.psu.edu/science-of-covid19
FoxNet is an individual-based modelling framework that can be customised to generate high-resolution red fox Vulpes vulpes population models for both northern and southern hemispheres. FoxNet predicts red fox population dynamics, including responses to control and landscape productivity. Model landscapes (up to ~15,000 km^2 and bait layouts can be generated within FoxNet or imported as GIS layers.
If you use FoxNet, please cite:
Hradsky BA, Kelly L, Robley A, Wintle BA (in review). FoxNet: an individual-based modelling framework to support red fox management. Journal of Applied Ecology.
A preliminary extension of the Hemelrijk 1996 model of reciprocal behavior to include feeding
Sean Barton | Published Monday, December 13, 2010 | Last modified Saturday, April 27, 2013A more complete description of the model can be found in Appendix I as an ODD protocol. This model is an expansion of the Hemelrijk (1996) that was expanded to include a simple food seeking behavior.
Anxiety-to-Approach Agent-Based Model (Netlogo)
Marie Lisa Kogler | Published Tuesday, April 04, 2023An Agent-Based Model to simulate agent reactions to threatening information based on the anxiety-to-approach framework of Jonas et al. (2014).
The model showcases the framework of BIS/BAS (inhibitory and approach motivated behavior) for the case of climate information, including parameters for anxiety, environmental awareness, climate scepticism and pro-environmental behavior intention.
Agents receive external information according to threat-level and information frequency. The population dynamic is based on the learning from that information as well as social contagion mechanisms through a scale-free network topology.
The model uses Netlogo 6.2 and the network extension.
…
Formal Organization Hierarchy and Informal Networks - "The Company Behind the Org Chart"
Tom Briggs | Published Sunday, April 18, 2021A generalized organizational agent- based model (ABM) containing both formal organizational hierarchy and informal social networks simulates organizational processes that occur over both formal network ties and informal networks.
Peer reviewed Evolution of Sex
Kristin Crouse | Published Sunday, June 05, 2016 | Last modified Wednesday, February 18, 2026Evolution of Sex is a NetLogo model that illustrates the advantages and disadvantages of sexual and asexual reproductive strategies. It seeks to demonstrate the answer to the question “Why do we have sex?”
A Data-Driven Approach of Layout Evaluation for Electric Vehicle Charging Infrastructure Using Agent-Based Simulation and GIS
yue zhang | Published Thursday, September 21, 2023The development and popularisation of new energy vehicles have become a global consensus. The shortage and unreasonable layout of electric vehicle charging infrastructure (EVCI) have severely restricted the development of electric vehicles. In the literature, many methods can be used to optimise the layout of charging stations (CSs) for producing good layout designs. However, more realistic evaluation and validation should be used to assess and validate these layout options. This study suggested an agent-based simulation (ABS) model to evaluate the layout designs of EVCI and simulate the driving and charging behaviours of electric taxis (ETs). In the case study of Shenzhen, China, GPS trajectory data were used to extract the temporal and spatial patterns of ETs, which were then used to calibrate and validate the actions of ETs in the simulation. The ABS model was developed in a GIS context of an urban road network with travelling speeds of 24 h to account for the effects of traffic conditions. After the high-resolution simulation, evaluation results of the performance of EVCI and the behaviours of ETs can be provided in detail and in summary. Sensitivity analysis demonstrates the accuracy of simulation implementation and aids in understanding the effect of model parameters on system performance. Maximising the time satisfaction of ET users and reducing the workload variance of EVCI were the two goals of a multiobjective layout optimisation technique based on the Pareto frontier. The location plans for the new CS based on Pareto analysis can significantly enhance both metrics through simulation evaluation.
Displaying 10 of 1190 results for "Ian M Hamilton" clear search