About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 136 results evolution clear search
Opportunity cost of walking away in the spatial iterated prisoner's dilemma
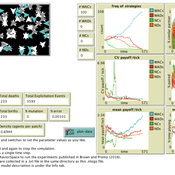
Luke Premo | Published Wednesday, April 03, 2019Previous work with the spatial iterated prisoner’s dilemma has shown that “walk away” cooperators are able to outcompete defectors as well as cooperators that do not respond to defection, but it remains to be seen just how robust the so-called walk away strategy is to ecologically important variables such as population density, error, and offspring dispersal. Our simulation experiments identify socio-ecological conditions in which natural selection favors strategies that emphasize forgiveness over flight in the spatial iterated prisoner’s dilemma. Our interesting results are best explained by considering how population density, error, and offspring dispersal affect the opportunity cost associated with walking away from an error-prone partner.
Toy Trader 2019
Timothy Gooding | Published Sunday, February 24, 2019A model that strips trade down to its core to explore foundational emergent behaviour and evolution in trade systems.
Adoption of a new regulation
Marco Janssen | Published Saturday, January 26, 2019A group of agents share a resource and agents will become sufficiently motivated to adopt a rule to constraint their freedom if they experience resource scarcity and developed mutual trust relationships.
The Evolution of Tribalism: A Social-Ecological Model of Cooperation and Inter-group Conflict Under Pastoralism
Nicholas Seltzer | Published Monday, January 21, 2019This study investigates a possible nexus between inter-group competition and intra-group cooperation, which may be called “tribalism.” Building upon previous studies demonstrating a relationship between the environment and social relations, the present research incorporates a social-ecological model as a mediating factor connecting both individuals and communities to the environment. Cyclical and non-cyclical fluctuation in a simple, two-resource ecology drive agents to adopt either “go-it-alone” or group-based survival strategies via evolutionary selection. Novelly, this simulation employs a multilevel selection model allowing group-level dynamics to exert downward selective pressures on individuals’ propensity to cooperate within groups. Results suggest that cooperation and inter-group conflict are co-evolved in a triadic relationship with the environment. Resource scarcity increases inter-group competition, especially when resources are clustered as opposed to widely distributed. Moreover, the tactical advantage of cooperation in the securing of clustered resources enhanced selective pressure on cooperation, even if that implies increased individual mortality for the most altruistic warriors. Troubling, these results suggest that extreme weather, possibly as a result of climate change, could exacerbate conflict in sensitive, weather-dependent social-ecologies—especially places like the Horn of Africa where ecologically sensitive economic modalities overlap with high-levels of diversity and the wide-availability of small arms. As well, global development and foreign aid strategists should consider how plans may increase the value of particular locations where community resources are built or aid is distributed, potentially instigating tribal conflict. In sum, these factors, interacting with pre-existing social dynamics dynamics, may heighten inter-ethnic or tribal conflict in pluralistic but otherwise peaceful communities.
For special issue submission in JASSS.
Co-evolution of mental models among socially learning agents
Garry Sotnik | Published Sunday, October 14, 2018The model simulates seven agents engaging in collective action and inter-network social learning. The objective of the model is to demonstrate how mental models of agents can co-evolve through a complex relationship among factors influencing decision-making, such as access to knowledge and personal- and group-level constraints.
The impact of potential crowd behaviours on emergency evacuation: an evolutionary game theoretic approach
Azhar Mohd Ibrahim | Published Monday, July 30, 2018Crowd dynamics have important applications in evacuation management systems relevant to organizing safer large scale gatherings. For crowd safety, it is very important to study the evolution of potential crowd behaviours by simulating the crowd evacuation process. Planning crowd control tasks by studying the impact of crowd behaviour evolution towards evacuation could mitigate the possibility of crowd disasters. During a typical emergency evacuation scenario, conflict among agents occurs when agents intend to move to the same location as a result of the interaction with their nearest neighbours. The effect of the agent response towards their neighbourhood is vital in order to understand the effect of variation of crowd behaviour on the whole environment. In this work, we model crowd motion subject to exit congestion under uncertainty conditions in a continuous space via computer simulations. We model best-response, risk-seeking, risk-averse and risk-neutral behaviours of agents via certain game theoretic notions. We perform computer simulations with heterogeneous populations in order to study the effect of the evolution of agent behaviours towards egress flow under threat conditions. Our simulation results show the relation between the local crowd pressure and the number of injured agents. We observe that when the proportion of agents in a population of risk-seeking agents is increased, the average crowd pressure, average local density and the number of injured agents increases. Besides that, based on our simulation results, we can infer that crowd disasters could be prevented if the agent population consists entirely of risk-averse and risk-neutral agents despite circumstances that lead to threats.
Social Closure and the Evolution of Cooperation via Indirect Reciprocity
Károly Takács Simone Righi | Published Saturday, June 09, 2018 | Last modified Saturday, June 09, 2018Righi S., Takacs K., Social Closure and the Evolution of Cooperation via Indirect Reciprocity, Resubmitted after Revisions to Scientific Reports
The Regional Security Game: An Agent-based, Evolutionary Model of Strategic Evolution and Stability
Anthony Skews | Published Saturday, June 09, 2018The Regional Security Game is a iterated public goods game with punishement based on based on life sciences work by Boyd et al. (2003 ) and Hintze & Adami (2015 ), with modifications appropriate for an international relations setting. The game models a closed regional system in which states compete over the distribution of common security benefits. Drawing on recent work applying cultural evolutionary paradigms in the social sciences, states learn through imitation of successful strategies rather than making instrumentally rational choices. The model includes the option to fit empirical data to the model, with two case studies included: Europe in 1933 on the verge of war and south-east Asia in 2013.
Potato late blight model
Francine Pacilly | Published Friday, April 13, 2018The purpose of the model is to simulate the spatial dynamics of potato late blight to analyse whether resistant varieties can be used effectively for sustainable disease control. The model represents an agricultural landscape with potato fields and data of a Dutch agricultural region is used as input for the model. We simulated potato production, disease spread and pathogen evolution during the growing season (April to September) for 36 years. Since late blight development and crop growth is weather dependent, measured weather data is used as model input. A susceptible and late blight resistant potato variety are distinguished. The resistant variety has a potentially lower yield but cannot get infected with the disease. However, during the growing season virulent spores can emerge as a result of mutations during spore production. This new virulent strain is able to infect the resistant fields, resulting in resistance breakdown. The model shows how disease severity, resistance durability and potato yield are affected by the fraction of fields across a landscape with a disease-resistant potato variety.
Peer reviewed Population Genetics
Kristin Crouse | Published Thursday, February 08, 2018 | Last modified Wednesday, September 09, 2020This model simulates the mechanisms of evolution, or how allele frequencies change in a population over time.
Displaying 10 of 136 results evolution clear search