About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 1170 results for "Aad Kessler" clear search
Retention in Higher Education: An Agent-Based Model of Social Interactions and Motivated Agent Behavior
Andrew Crooks Amira Al-Khulaidy Stine | Published Wednesday, October 23, 2024Educational attainment and student retention in higher education are two of the main focuses of higher education research. Institutions in the U.S. are constantly looking for ways to identify areas of improvement across different aspects of the student experience on university campuses. This paper combines Department of Education data, U.S. Census data, and higher education theory on student retention, to build an agent-based model of student behavior.
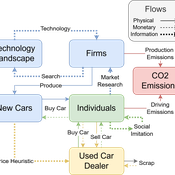
Driving in the wrong direction? A co-evolutionary model of electric vehicle adoption and innovation
Daniel Torren-Peraire | Published Friday, July 11, 2025Car-centric societies face substantial challenges in moving towards sustainable
mobility systems, with internal combustion engine vehicles remaining a major
source of emissions. Electric vehicles play a critical role in addressing this challenge, yet their diffusion depends on the interaction of consumer behaviour, firm
innovation, and policy incentives. This paper develops an agent-based model to
examine these dynamics, calibrated on the data for the state of California over
2001-2023. In the model, heterogeneous car users influenced by their social peers
…
Netlogo model ` Effect of Network Homophily and Partisanship on Social Media to “Oil Spill” Polarizations’
takuya nagura | Published Saturday, September 13, 2025This model was utilized for the simulation in the paper titled Effect of Network Homophily and Partisanship on Social Media to “Oil Spill” Polarizations. It allows you to examine whether oil spill polarization occurs through people’s communication under various conditions.
・Choose the network construction conditions you’d like to examine from the “rewire-style” chooser box.
・Select the desired strength of partisanship from the “partisanlevel” chooser box. You can also set the strength manually in the code tab.
・You can set the number of dynamic topics using the “number-of-topics” slider.
・Use the “divers-of-opinion” slider to set the number of preference types for each dynamic topic.
…
The dynamic agent-based model of market of single commodity and process of setting of prices
Mark Voronovitsky | Published Saturday, January 24, 2009 | Last modified Saturday, April 27, 2013The dynamic agent based model of system which turn out the self-adjusting system, are considered in this text.
Will it spread or not? The effects of social influences and network topology on innovation diffusion
Sebastiano Delre | Published Monday, October 24, 2011 | Last modified Saturday, April 27, 2013This models simulates innovation diffusion curves and it tests the effects of the degree and the direction of social influences. This model replicates, extends and departs from classical percolation models.
In-group favoritism due to friend selection strategies based on fixed tag and within-group reputation
Yutaka Nakai | Published Friday, March 28, 2014 | Last modified Friday, March 28, 2014An agent-based model simulates emergence of in-group favoritism. Agents adopt friend selection strategies using an invariable tag and reputations meaning how cooperative others are to a group. The reputation can be seen as a kind of public opinion.
External shocks, agent interactions, and endogenous feedbacks--investigating system resilience with a stylized land use model
Yang Chen | Published Tuesday, March 06, 2018The purpose of the presented ABM is to explore how system resilience is affected by external disturbances and internal dynamics by using the stylized model of an agricultural land use system.
We explore land system resilience with a stylized land use model in which agents’ land use activities are affected by external shocks, agent interactions, and endogenous feedbacks. External shocks are designed as yield loss in crops, which is ubiquitous in almost every land use system where perturbations can occur due to e.g. extreme weather conditions or diseases. Agent interactions are designed as the transfer of buffer capacity from farmers who can and are willing to provide help to other farmers within their social network. For endogenous feedbacks, we consider land use as an economic activity which is regulated by markets — an increase in crop production results in lower price (a negative feedback) and an agglomeration of a land use results in lower production costs for the land use type (a positive feedback).
The Evolution of Tribalism: A Social-Ecological Model of Cooperation and Inter-group Conflict Under Pastoralism
Nicholas Seltzer | Published Monday, January 21, 2019This study investigates a possible nexus between inter-group competition and intra-group cooperation, which may be called “tribalism.” Building upon previous studies demonstrating a relationship between the environment and social relations, the present research incorporates a social-ecological model as a mediating factor connecting both individuals and communities to the environment. Cyclical and non-cyclical fluctuation in a simple, two-resource ecology drive agents to adopt either “go-it-alone” or group-based survival strategies via evolutionary selection. Novelly, this simulation employs a multilevel selection model allowing group-level dynamics to exert downward selective pressures on individuals’ propensity to cooperate within groups. Results suggest that cooperation and inter-group conflict are co-evolved in a triadic relationship with the environment. Resource scarcity increases inter-group competition, especially when resources are clustered as opposed to widely distributed. Moreover, the tactical advantage of cooperation in the securing of clustered resources enhanced selective pressure on cooperation, even if that implies increased individual mortality for the most altruistic warriors. Troubling, these results suggest that extreme weather, possibly as a result of climate change, could exacerbate conflict in sensitive, weather-dependent social-ecologies—especially places like the Horn of Africa where ecologically sensitive economic modalities overlap with high-levels of diversity and the wide-availability of small arms. As well, global development and foreign aid strategists should consider how plans may increase the value of particular locations where community resources are built or aid is distributed, potentially instigating tribal conflict. In sum, these factors, interacting with pre-existing social dynamics dynamics, may heighten inter-ethnic or tribal conflict in pluralistic but otherwise peaceful communities.
For special issue submission in JASSS.
Sensitivity of a population submitted to floods to unknown upcoming floods and parameters of the dynamics
Sylvie Huet | Published Wednesday, September 22, 2021This work is a java implementation of a study of the viability of a population submitted to floods. The population derives some benefit from living in a certain environment. However, in this environment, floods can occur and cause damage. An individual protection measure can be adopted by those who wish and have the means to do so. The protection measure reduces the damage in case of a flood. However, the effectiveness of this measure deteriorates over time. Individual motivation to adopt this measure is boosted by the occurrence of a flood. Moreover, the public authorities can encourage the population to adopt this measure by carrying out information campaigns, but this comes at a cost. People’s decisions are modelled based on the Protection Motivation Theory (Rogers1975, Rogers 1997, Maddux1983) arguing that the motivation to protect themselves depends on their perception of risk, their capacity to cope with risk and their socio-demographic characteristics.
While the control designing proper informations campaigns to remain viable every time is computed in the work presented in https://www.comses.net/codebases/e5c17b1f-0121-4461-9ae2-919b6fe27cc4/releases/1.0.0/, the aim of the present work is to produce maps of probable viability in case the serie of upcoming floods is unknown as well as much of the parameters for the population dynamics. These maps are bi-dimensional, based on the value of known parameters: the current average wealth of the population and their actual or possible future annual revenues.
The impact of scientific networks, affinity bias and scientific uncertainty on the public uptake of science
Sacha Ferrari | Published Thursday, January 23, 2025Ferrari, S., Lammers, W., Wenmackers, S. (forthcoming) How the structure of scientific communities could impact the public uptake of uncertain science. Philosophy of Science.
Displaying 10 of 1170 results for "Aad Kessler" clear search