About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 38 results for "Christopher Roberts" clear search
Informal Information Transmission Networks among Medieval Genoese Investors
Christopher Frantz | Published Wednesday, October 09, 2013 | Last modified Thursday, October 24, 2013This model represents informal information transmission networks among medieval Genoese investors used to inform each other about cheating merchants they employed as part of long-distance trade operations.
SugarscapeCW
Christopher Watts | Published Saturday, August 01, 2015 | Last modified Wednesday, April 12, 2023A replication in Netlogo 5.2 of the classic model, Sugarscape (Epstein & Axtell, 1996).
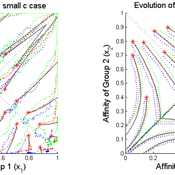
Affinity/Hostility in Divided Communities
Christopher Thron | Published Friday, January 22, 2016Agent-based model of intergroup conflict in divided communities.
Agent-based simulation of small group decision-making under no communication
Christopher Poile | Published Thursday, May 26, 2016A computational model of a classic small group study by Alex Bavelas. This computational model was designed to explore the difficulty in translating a seemingly simple real-world experiment into a computational model.
Pollution-development Tradeoffs in Nigeria--an Agent-based Model
Christopher Thron | Published Thursday, June 03, 2021Like many developing countries, Nigeria is faced with a number of tradeoffs that pit rapid economic development against environmental preservation. Environmentally sustainable, “green” economic development is slower, more costly, and more difficult than unrestricted, unregulated economic growth. The mathematical model that we develop in this code suggests that widespread public awareness of environmental issues is insufficient to prevent the tendency towards sacrificing the environment for the sake of growth. Even if people have an understanding of negative impacts and always choose to act in their own self-interest, they may still act collectively in such a way as to bring down the quality of life for the entire society. We conclude that additional actions must be taken besides raising public awareness of the environmental problem.
Animal territory formation (Reusable Building Block RBB)
Volker Grimm Stephanie Kramer-Schadt Robert Zakrzewski | Published Sunday, November 12, 2023This is a generic sub-model of animal territory formation. It is meant to be a reusable building block, but not in the plug-and-play sense, as amendments are likely to be needed depending on the species and region. The sub-model comprises a grid of cells, reprenting the landscape. Each cell has a “quality” value, which quantifies the amount of resources provided for a territory owner, for example a tiger. “Quality” could be prey density, shelter, or just space. Animals are located randomly in the landscape and add grid cells to their intial cell until the sum of the quality of all their cells meets their needs. If a potential new cell to be added is owned by another animal, competition takes place. The quality values are static, and the model does not include demography, i.e. mortality, mating, reproduction. Also, movement within a territory is not represented.
Sensitivity of a population submitted to floods to unknown upcoming floods and parameters of the dynamics
Sylvie Huet | Published Wednesday, September 22, 2021This work is a java implementation of a study of the viability of a population submitted to floods. The population derives some benefit from living in a certain environment. However, in this environment, floods can occur and cause damage. An individual protection measure can be adopted by those who wish and have the means to do so. The protection measure reduces the damage in case of a flood. However, the effectiveness of this measure deteriorates over time. Individual motivation to adopt this measure is boosted by the occurrence of a flood. Moreover, the public authorities can encourage the population to adopt this measure by carrying out information campaigns, but this comes at a cost. People’s decisions are modelled based on the Protection Motivation Theory (Rogers1975, Rogers 1997, Maddux1983) arguing that the motivation to protect themselves depends on their perception of risk, their capacity to cope with risk and their socio-demographic characteristics.
While the control designing proper informations campaigns to remain viable every time is computed in the work presented in https://www.comses.net/codebases/e5c17b1f-0121-4461-9ae2-919b6fe27cc4/releases/1.0.0/, the aim of the present work is to produce maps of probable viability in case the serie of upcoming floods is unknown as well as much of the parameters for the population dynamics. These maps are bi-dimensional, based on the value of known parameters: the current average wealth of the population and their actual or possible future annual revenues.
Agent-based model of WiFi tracking system in urban environment
Christopher Thron Khoi Tran | Published Friday, April 21, 2017This code simulates the WiFi user tracking system described in: Thron et al., “Design and Simulation of Sensor Networks for Tracking Wifi Users in Outdoor Urban Environments”. Testbenches used to create the figures in the paper are included.
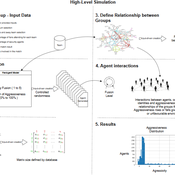
Identity Fusion Group Behaviour Simulator
Leonardo D. Martins Araujo Roberto Cesar Betini | Published Monday, June 03, 2024The model is based on Swann and Buhrmester’s Identity Fusion behavioural theory, which seeks to explain why an individual puts the group’s priorities above their personal expectations. In order to observe the theory and validate group behaviour, a case study was carried out focusing on scenarios of group violence in football stadiums in Brazil. For the modelling, each agent has a distribution of levels of identification with the group to which they belong, with their level of fusion varying between 1 and 5. According to behavioural theory, an individual’s degree of fusion with the group directly interferes with their behaviour of replicating actions and absorbing group beliefs.
Social model of a Team Developing a Planning-Methodology
Oswaldo Terán Christophe Sibertin | Published Monday, November 18, 2013 | Last modified Sunday, November 16, 2014The model represents a team intended at designing a methodology for Institutional Planning. Included in ICAART’14 to exemplify how emotions can be identified in SocLab; and in ESSA’14 to show the Efficiency of Organizational Withdrawal vs Commitment.
Displaying 10 of 38 results for "Christopher Roberts" clear search