About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 21 results game theory clear search
Status hierarchies and the emergence of cooperation in task groups
Hsuan-Wei Lee | Published Thursday, January 02, 2025This repository contains an agent-based simulation model exploring how status hierarchies influence the emergence and sustainability of cooperation in task-oriented groups. The model builds on evolutionary game theory to examine the dynamics of cooperation under single-leader and multi-leader hierarchies, investigating factors such as group size, assortativity, and hierarchical clarity. Key findings highlight the trade-offs between different leadership structures in fostering group cooperation and reveal the conditions under which cooperation is most stable.
The repository includes code for simulations, numerical analysis scripts, and visualization tools to replicate the results presented in the manuscript titled “Status hierarchies and the emergence of cooperation in task groups.”
Feel free to explore, reproduce the findings, or adapt the model for further research!
Using Agent-Based Modelling and Reinforcement Learning to Study Hybrid Threats
kpadur | Published Friday, September 20, 2024Hybrid attacks coordinate the exploitation of vulnerabilities across domains to undermine trust in authorities and cause social unrest. Whilst such attacks have primarily been seen in active conflict zones, there is growing concern about the potential harm that can be caused by hybrid attacks more generally and a desire to discover how better to identify and react to them. In addressing such threats, it is important to be able to identify and understand an adversary’s behaviour. Game theory is the approach predominantly used in security and defence literature for this purpose. However, the underlying rationality assumption, the equilibrium concept of game theory, as well as the need to make simplifying assumptions can limit its use in the study of emerging threats. To study hybrid threats, we present a novel agent-based model in which, for the first time, agents use reinforcement learning to inform their decisions. This model allows us to investigate the behavioural strategies of threat agents with hybrid attack capabilities as well as their broader impact on the behaviours and opinions of other agents.
Peer reviewed A Bayesian Nash Equilibrium (BNE)-informed ABM for pedestrian evacuation in different constricted spaces
Jiaqi Ge Yiyu Wang Alexis Comber | Published Wednesday, October 11, 2023This BNE-informed ABM ultimately aims to provide a more realistic description of complicated pedestrian behaviours especially in high-density and life-threatening situations. Bayesian Nash Equilibrium (BNE) was adopted to reproduce interactive decision-making process among rational and game-playing agents. The implementations of 3 behavioural models, which are Shortest Route (SR) model, Random Follow (RF) model, and BNE model, make it possible to simulate emergent patterns of pedestrian behaviours (e.g. herding and self-organised queuing behaviours, etc.) in emergency situations.
According to the common features of previous mass trampling accidents, a series of simulation experiments were performed in space with 3 types of barriers, which are Horizontal Corridors, Vertical Corridors, and Random Squares, standing for corridors, bottlenecks and intersections respectively, to investigate emergent behaviours of evacuees in varied constricted spatial environments. The output of this ABM has been available at https://data.mendeley.com/datasets/9v4byyvgxh/1.
Simulation Experiments of "The dynamics of corruption under an optional external supervision service"
Xin Zhou | Published Wednesday, June 21, 2023The simulation experiment is for studying the influence of external supervision services on combating corruption.
Algorithm: evolutionary game theory
Peer reviewed Dynamic Equilibria Prediction: Experience-Weighted Attraction (EWA), Python Implementation
Vinicius Ferraz | Published Friday, December 02, 2022This project is based on a Jupyter Notebook that describes the stepwise implementation of the EWA model in bi-matrix ( 2×2 ) strategic-form games for the simulation of economic learning processes. The output is a dataset with the simulated values of Attractions, Experience, selected strategies, and payoffs gained for the desired number of rounds and periods. The notebook also includes exploratory data analysis over the simulated output based on equilibrium, strategy frequencies, and payoffs.
Peer reviewed An agent-based simulation model of pedestrian evacuation based on Bayesian Nash Equilibrium
Jiaqi Ge Yiyu Wang Alexis Comber | Published Wednesday, July 06, 2022This ABM aims to introduce a new individual decision-making model, BNE into the ABM of pedestrian evacuation to properly model individual behaviours and motions in emergency situations. Three types of behavioural models has been developed, which are Shortest Route (SR) model, Random Follow (RF) model, and BNE model, to better reproduce evacuation dynamics in a tunnel space. A series of simulation experiments were conducted to evaluate the simulating performance of the proposed ABM.
ICARUS - a multi-agent compliance inspection model
Slaven Smojver | Published Monday, May 09, 2022ICARUS is a multi-agent compliance inspection model (ICARUS - Inspecting Compliance to mAny RUleS). The model is applicable to environments where an inspection agency, via centrally coordinated inspections, examines compliance in organizations which must comply with multiple provisions (rules). The model (ICARUS) contains 3 types of agents: entities, inspection agency and inspectors / inspections. ICARUS describes a repeated, simultaneous, non-cooperative game of pure competition. Agents have imperfect, incomplete, asymmetric information. Entities in each move (tick) choose a pure strategy (comply/violate) for each rule, depending on their own subjective assessment of the probability of the inspection. The Inspection Agency carries out the given inspection strategy.
A more detailed description of the model is available in the .nlogo file.
Full description of the model (in line with the ODD+D protocol) and the analysis of the model (including verification, validation and sensitivity analysis) can be found in the attached documentation.
Peer reviewed Evolutionary Economic Learning Simulation: A Genetic Algorithm for Dynamic 2x2 Strategic-Form Games in Python
Vinicius Ferraz Thomas Pitz | Published Friday, April 08, 2022This project combines game theory and genetic algorithms in a simulation model for evolutionary learning and strategic behavior. It is often observed in the real world that strategic scenarios change over time, and deciding agents need to adapt to new information and environmental structures. Yet, game theory models often focus on static games, even for dynamic and temporal analyses. This simulation model introduces a heuristic procedure that enables these changes in strategic scenarios with Genetic Algorithms. Using normalized 2x2 strategic-form games as input, computational agents can interact and make decisions using three pre-defined decision rules: Nash Equilibrium, Hurwicz Rule, and Random. The games then are allowed to change over time as a function of the agent’s behavior through crossover and mutation. As a result, strategic behavior can be modeled in several simulated scenarios, and their impacts and outcomes can be analyzed, potentially transforming conflictual situations into harmony.
Human-in-the-loop Experiment of the Strategic Coalition Formation using the glove game
Andrew Collins | Published Monday, November 23, 2020 | Last modified Wednesday, June 22, 2022The purpose of the model is to collect information on human decision-making in the context of coalition formation games. The model uses a human-in-the-loop approach, and a single human is involved in each trial. All other agents are controlled by the ABMSCORE algorithm (Vernon-Bido and Collins 2020), which is an extension of the algorithm created by Collins and Frydenlund (2018). The glove game, a standard cooperative game, is used as the model scenario.
The intent of the game is to collection information on the human players behavior and how that compares to the computerized agents behavior. The final coalition structure of the game is compared to an ideal output (the core of the games).
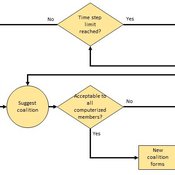
Heuristic Algorithm for Generating Strategic Coalition Structures
Andrew Collins Daniele Vernon-Bido | Published Monday, October 12, 2020The purpose of the model is to generate coalition structures of different glove games, using a specially designed algorithm. The coalition structures can be are later analyzed by comparing them to core partitions of the game used. Core partitions are coalition structures where no subset of players has an incentive to form a new coalition.
The algorithm used in this model is an advancement of the algorithm found in Collins & Frydenlund (2018). It was used used to generate the results in Vernon-Bido & Collins (2021).
Displaying 10 of 21 results game theory clear search