About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 233 results other clear search
Human-in-the-loop Experiment of the Strategic Coalition Formation using the glove game
Andrew Collins | Published Monday, November 23, 2020 | Last modified Wednesday, June 22, 2022The purpose of the model is to collect information on human decision-making in the context of coalition formation games. The model uses a human-in-the-loop approach, and a single human is involved in each trial. All other agents are controlled by the ABMSCORE algorithm (Vernon-Bido and Collins 2020), which is an extension of the algorithm created by Collins and Frydenlund (2018). The glove game, a standard cooperative game, is used as the model scenario.
The intent of the game is to collection information on the human players behavior and how that compares to the computerized agents behavior. The final coalition structure of the game is compared to an ideal output (the core of the games).
Bayesian Updating Opinion Shared Uncertainty Model.
Johnathan Adams | Published Monday, November 16, 2020 | Last modified Friday, May 14, 2021This is an opinion dynamics model which extends the model found in (Martins 2009). The previous model had an unshared uncertainty assumption in agent-to-agent interaction this model relaxes that assumption. The model only supports a fully connect network where every agent has an equal likelihood of interacting with every other agent at any given time step. The model is highly modular so different social network paradigm can easier be implemented.
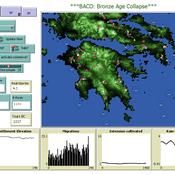
The Bronze Age Collapse model (BACO model)
Marco Vidal-Cordasco | Published Friday, October 09, 2020The Bronze Age Collapse model (BACO model) is written using free NetLogo software v.6.0.3. The purpose of using the BACO model is to develop a tool to identify and analyse the main factors that made the Late Bronze Age and Early Iron Age socio-ecological system resilient or vulnerable in the face of the environmental aridity recorded in the Aegean. The model explores the relationship between dependent and independent variables. Independent variables are: a) inter-annual rainfall variability for the Late Bronze Age and Early Iron Age in the eastern Mediterranean, b) intensity of raiding, c) percentage of marine, agricultural and other calorie sources included in the diet, d) soil erosion processes, e) farming assets, and d) storage capacity. Dependent variables are: a) human pressure for land, b) settlement patterns, c) number of commercial exchanges, d) demographic behaviour, and e) number of migrations.
Opinion dynamics and collective risk perception: An ABM model of institutional and media communication about disasters - Code and Datasets
danielevilone | Published Tuesday, October 06, 2020The O.R.E. (Opinions on Risky Events) model describes how a population of interacting individuals process information about a risk of natural catastrophe. The institutional information gives the official evaluation of the risk; the agents receive this communication, process it and also speak to each other processing further the information. The description of the algorithm (as it appears also in the paper) can be found in the attached file OREmodel_description.pdf.
The code (ORE_model.c), written in C, is commented. Also the datasets (inputFACEBOOK.txt and inputEMAILs.txt) of the real networks utilized with this model are available.
For any questions/requests, please write me at [email protected]
Peer reviewed An Agent-Based Model of Campaign-Based Watershed Management
Samuel Assefa Aad Kessler Luuk Fleskens | Published Monday, September 21, 2020 | Last modified Friday, June 04, 2021The model simulates the national Campaign-Based Watershed Management program of Ethiopia. It includes three agents (farmers, Kebele/ village administrator, extension workers) and the physical environment that interact with each other. The physical environment is represented by patches (fields). Farmers make decisions on the locations of micro-watersheds to be developed, participation in campaign works to construct soil and water conservation structures, and maintenance of these structures. These decisions affect the physical environment or generate model outcomes. The model is developed to explore conditions that enhance outcomes of the program by analyzing the effect on the area of land covered and quality of soil and water conservation structures of (1) enhancing farmers awareness and motivation, (2) establishing and strengthening micro-watershed associations, (3) introducing alternative livelihood opportunities, and (4) enhancing the commitment of local government actors.
Leviathan model and its approximation
Thibaut Roubin Guillaume Deffuant | Published Thursday, September 17, 2020 | Last modified Monday, September 06, 2021The model is based on the influence function of the Leviathan model (Deffuant, Carletti, Huet 2013 and Huet and Deffuant 2017). We aim at better explaining some patterns generated by this model, using a derived mathematical approximation of the evolution of the opinions averaged.
We consider agents having an opinion/esteem about each other and about themselves. During dyadic meetings, agents change their respective opinion about each other, and possibly about other agents they gossip about, with a noisy perception of the opinions of their interlocutor. Highly valued agents are more influential in such encounters.
We show that the inequality of reputations among agents have a negative effect on the opinions about the agents of low status.The mathematical analysis of the opinion dynamic shows that the lower the status of the agent, the more detrimental the interactions are for the opinions about this agent, especially when gossip is activated, while the interactions always tend to increase the opinions about agents of high status.
The uFUNK Model
Davide Secchi | Published Monday, August 31, 2020The agent-based simulation is set to work on information that is either (a) functional, (b) pseudo-functional, (c) dysfunctional, or (d) irrelevant. The idea is that a judgment on whether information falls into one of the four categories is based on the agent and its network. In other words, it is the agents who interprets a particular information as being (a), (b), (c), or (d). It is a decision based on an exchange with co-workers. This makes the judgment a socially-grounded cognitive exercise. The uFUNK 1.0.2 Model is set on an organization where agent-employee work on agent-tasks.
Wildlife-Human Interactions in Shared Landscapes (WHISL)
Nicholas Magliocca Neil Carter Andres Baeza-Castro | Published Friday, May 22, 2020This model simulates a group of farmers that have encounters with individuals of a wildlife population. Each farmer owns a set of cells that represent their farm. Each farmer must decide what cells inside their farm will be used to produce an agricultural good that is self in an external market at a given price. The farmer must decide to protect the farm from potential encounters with individuals of the wildlife population. This decision in the model is called “fencing”. Each time that a cell is fenced, the chances of a wildlife individual to move to that cell is reduced. Each encounter reduces the productive outcome obtained of the affected cell. Farmers, therefore, can reduce the risk of encounters by exclusion. The decision of excluding wildlife is made considering the perception of risk of encounters. In the model, the perception of risk is subjective, as it depends on past encounters and on the perception of risk from other farmers in the community. The community of farmers passes information about this risk perception through a social network. The user (observer) of the model can control the importance of the social network on the individual perception of risk.
The Coevolution of the Firm and the Product Attribute Space
César García-Díaz | Published Friday, May 22, 2020This model inspects the performance of firms as the product attribute space changes, which evolves as a consequence of firms’ actions. Firms may create new product variants by dragging demand from other existing variants. Firms decide whether to open new product variants, to invade existing ones, or to keep their variant portfolio. At each variant there is a Cournot competition each round. Competition is nested since many firms compete at many variants simultaneously, affecting firm composition at each location (variant).
After the Cournot outcomes, at each round firms decide whether to (i) keep their existing product variant niche, (ii) invade an existing variant, (iii) create a new variant, or (iv) abandon a variant. Firms’ profits across their niche take into consideration the niche-width cost and the cost of opening a new variant.
Introduction of a contact tracking app for outbreak control
Tim Verwaart | Published Tuesday, April 21, 2020The application of a smartphone application to register physical encounters between individuals is considered by public health authorities, as a means to reduce the number of infections in the 2020 COVID-19 pandemic. The general idea is that continuous registration of all other smartphones in the vicinity of an individual’s smartphone potentially enables early warning of the owners of the other smartphones, in case the individual is tested positive as infected. Those other individuals can then go into isolation and be considered for testing. The purpose of the present simulation is to explore the potential effects of this application on frequencies of infection, isolation, and positive and negative infection test results.
Displaying 10 of 233 results other clear search