About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 109 results for "Steven Dalderop" clear search
EthnoCultural Tag model (ECT)
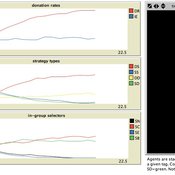
Bruce Edmonds David Hales | Published Friday, October 16, 2015 | Last modified Wednesday, May 09, 2018Captures interplay between fixed ethnic markers and culturally evolved tags in the evolution of cooperation and ethnocentrism. Agents evolve cultural tags, behavioural game strategies and in-group definitions. Ethnic markers are fixed.
Reflexivity in a diffusion of innovations model
César García-Díaz Carlos Cordoba | Published Thursday, May 07, 2020In this agent-based model, agents decide to adopt a new product according to a utility function that depends on two kinds of social influences. First, there is a local influence exerted on an agent by her closest neighbors that have already adopted, and also by herself if she feels the product suits her personal needs. Second, there is a global influence which leads agents to adopt when they become aware of emerging trends happening in the system. For this, we endow agents with a reflexive capacity that allows them to recognize a trend, even if they can not perceive a significant change in their neighborhood.
Results reveal the appearance of slowdown periods along the adoption rate curve, in contrast with the classic stylized bell-shaped behavior. Results also show that network structure plays an important role in the effect of reflexivity: while some structures (e.g., scale-free networks) may amplify it, others (e.g., small-world structure) weaken such an effect.
PaCE Austria Pilot Model
Ruth Meyer | Published Tuesday, June 30, 2020The objective of building a social simulation in the Populism and Civic Engagement (PaCE) project is to study the phenomenon of populism by mapping individual level political behaviour and explain the influence of agents on, and their interdependence with the respective political parties. Voters, political parties and – to some extent – the media can be viewed as forming a complex adaptive system, in which parties compete for citizens’ votes, voters decide on which party to vote for based on their respective positions with regard to particular issues, and the media may influence the salience of issues in the public debate.
This is the first version of a model exploring voting behaviour in Austria. It focusses on modelling the interaction of voters and parties in a political landscape; the effects of the media are not yet represented. Austria was chosen as a case study because it has an established populist party (the “Freedom Party” FPO), which has even been part of the government over the years.
Peer reviewed Are Countertrade credits as flexible and efficient as cash? A novel approach to reducing income inequality using countertrade methodology.
Peter Malliaros | Published Monday, May 03, 2021 | Last modified Tuesday, May 11, 2021The impacts of income inequality can be seen everywhere, regardless of the country or the level of economic development. According to the literature review, income inequality has negative impacts in economic, social, and political variables. Notwithstanding of how well or not countries have done in reducing income inequality, none have been able to reduce it to a Gini Coefficient level of 0.2 or less.
This is the promise that a novel approach called Counterbalance Economics (CBE) provides without the need of increased taxes.
Based on the simulation, introducing the CBE into the Australian, UK, US, Swiss or German economies would result in an overall GDP increase of under 1% however, the level of inequality would be reduced from an average of 0.33 down to an average of 0.08. A detailed explanation of how to use the model, software, and data dependencies along with all other requirements have been included as part of the info tab in the model.
Models associated with paper entitled "Polarization in Social Media: A Virtual Worlds-Based Approach"
Sven Banisch Dennis Jacob | Published Thursday, June 22, 2023This model contains MATLAB code describing the virtual worlds framework used in the paper entitled “Polarization in Social Media: A Virtual Worlds-Based Approach.” The parent directory contains driver code for replicating results from the paper. Additionally, the source code is structured by three directories:
- Data Structures: Contains classes and objects used in the code, such as the virtualWorlds.m
- Metrics: Contains code which computes metrics, such as congruentLinks.m
- Visualization: Contains code for generating pictures and plots, such as drawSystemState.m
…
Foundress dilemma model
Marco Janssen Takao Sasaki Zachary Joseph Shaffer Stephen Pratt Brian Haney Jennifer Fewell | Published Thursday, July 28, 2016A haystack-style model of group selection to capture the essential features of colony foundation for queens of the ant based on observation of the ant Pogonomyrmex californicus.
Last Mile Commuter Behavior Model
Dean Massey Moira Zellner Yoram Shiftan Jonathan Levine Maria Arquero | Published Friday, November 07, 2014 | Last modified Friday, November 07, 2014We represent commuters and their preferences for transportation cost, time and safety. Agents assess their options via their preferences, their environment, and the modes available. The model has policy levers to test impact on last-mile problem.
Spatial model of the noisy Prisoner's Dilemma with reward shift
Matus Halas | Published Thursday, March 05, 2015 | Last modified Tuesday, May 29, 2018Interactions of players embedded in a closed square lattice are determined by distance and overall gains and they lead to shifts of reward payoff between temptation and punishment. A new winner balancing against threats is ultimately discovered.
Using Agent-Based Modelling and Reinforcement Learning to Study Hybrid Threats
kpadur | Published Friday, September 20, 2024Hybrid attacks coordinate the exploitation of vulnerabilities across domains to undermine trust in authorities and cause social unrest. Whilst such attacks have primarily been seen in active conflict zones, there is growing concern about the potential harm that can be caused by hybrid attacks more generally and a desire to discover how better to identify and react to them. In addressing such threats, it is important to be able to identify and understand an adversary’s behaviour. Game theory is the approach predominantly used in security and defence literature for this purpose. However, the underlying rationality assumption, the equilibrium concept of game theory, as well as the need to make simplifying assumptions can limit its use in the study of emerging threats. To study hybrid threats, we present a novel agent-based model in which, for the first time, agents use reinforcement learning to inform their decisions. This model allows us to investigate the behavioural strategies of threat agents with hybrid attack capabilities as well as their broader impact on the behaviours and opinions of other agents.
Hybrid agent-based methodology for testing response protocols
Fernando Sancho Caparrini | Published Wednesday, February 03, 2021In recent years we have seen multiple incidents with a large number of people injured and killed by one or more armed attackers. Since this type of violence is difficult to predict, detecting threats as early as possible allows to generate early warnings and reduce response time. In this context, any tool to check and compare different action protocols can be a further step in the direction of saving lives. Our proposal combines features from continuous and discrete models to obtain the best of both worlds in order to simulate large and crowded spaces where complex behavior individuals interact. With this proposal we aim to provide a tool for testing different security protocols under several emergency scenarios, where spaces, hazards, and population can be customized. Finally, we use a proof of concept implementation of this model to test specific security protocols under emergency situations for real spaces. Specifically, we test how providing some users of a university college with an app that informs about the type and characteristics of the ongoing hazard, affects in the safety performance.
Displaying 10 of 109 results for "Steven Dalderop" clear search