About the CoMSES Model Library more info
Our mission is to help computational modelers develop, document, and share their computational models in accordance with community standards and good open science and software engineering practices. Model authors can publish their model source code in the Computational Model Library with narrative documentation as well as metadata that supports open science and emerging norms that facilitate software citation, computational reproducibility / frictionless reuse, and interoperability. Model authors can also request private peer review of their computational models. Models that pass peer review receive a DOI once published.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and feel free to contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 26 results survival clear search
Structural Violence and Neurobiological Adaptation: Modeling the Trajectory of Youth Outside of Care
masterpiece33330-prog | Published Thursday, November 27, 2025This study presents a System Dynamics (SD) model that explores the “trajectories of homelessness” among youth outside of the formal care system. Unlike traditional approaches that view runaway behavior as a discrete choice, this model reinterprets it as a neurobiological adaptation to chronic resource deprivation and systemic neglect.
The model incorporates key mechanisms such as ‘Allostatic Load’ accumulation, ‘PFC-Amygdala Switching’, and the ‘Iatrogenic Effects’ of shelter policies. It utilizes Monte Carlo simulations to demonstrate how structural factors create a “probabilistic vulnerability,” trapping youth in cycles of survival crime and isolation regardless of individual resilience.
The uploaded code includes a Python implementation of the model to ensure reproducibility of the stochastic analysis presented in the paper.
Peer reviewed Environmental stochasticity, resource heterogeneity, and the evolution of cooperation
Michaela Starkey Colin Lynch Terry Hunt Carl Lipo | Published Friday, March 14, 2025 | Last modified Wednesday, July 30, 2025The emergence of cooperation in human societies is often linked to environmental constraints, yet the specific conditions that promote cooperative behavior remain an open question. This study examines how resource unpredictability and spatial dispersion influence the evolution of cooperation using an agent-based model (ABM). Our simulations test the effects of rainfall variability and resource distribution on the survival of cooperative and non-cooperative strategies. The results show that cooperation is most likely to emerge when resources are patchy, widely spaced, and rainfall is unpredictable. In these environments, non-cooperators rapidly deplete local resources and face high mortality when forced to migrate between distant patches. In contrast, cooperators—who store and share resources—can better endure extended droughts and irregular resource availability. While rainfall stochasticity alone does not directly select for cooperation, its interaction with resource patchiness and spatial constraints creates conditions where cooperative strategies provide a survival advantage. These findings offer broader insights into how environmental uncertainty shapes social organization in resource-limited settings. By integrating ecological constraints into computational modeling, this study contributes to a deeper understanding of the conditions that drive cooperation across diverse human and animal systems.
This paper presents an agent-based model to study the dynamics of city-state systems in a constrained environment with limited space and resources. The model comprises three types of agents: city-states, villages, and battalions, where city-states, the primary decision-makers, can build villages for food production and recruit battalions for defense and aggression. In this setting, simulation results, generated through a multi-parameter grid sampling, suggest that risk-seeking strategies are more effective in high-cost scenarios, provided that the production rate is sufficiently high. Also, the model highlights the role of output productivity in defining which strategic preferences are successful in a long-term scenario, with higher outputs supporting more aggressive expansion and military actions, while resource limitations compel more conservative strategies focused on survival and resource conservation. Finally, the results suggest the existence of a non-linear effect of diminishing returns in strategic investments on successful strategies, emphasizing the need for careful resource allocation in a competitive environment.
Peer reviewed MADTOR: Model for Assessing Drug Trafficking Organizations Resilience
Deborah Manzi | Published Friday, February 23, 2024Criminal organizations operate in complex changing environments. Being flexible and dynamic allows criminal networks not only to exploit new illicit opportunities but also to react to law enforcement attempts at disruption, enhancing the persistence of these networks over time. Most studies investigating network disruption have examined organizational structures before and after the arrests of some actors but have disregarded groups’ adaptation strategies.
MADTOR simulates drug trafficking and dealing activities by organized criminal groups and their reactions to law enforcement attempts at disruption. The simulation relied on information retrieved from a detailed court order against a large-scale Italian drug trafficking organization (DTO) and from the literature.
The results showed that the higher the proportion of members arrested, the greater the challenges for DTOs, with higher rates of disrupted organizations and long-term consequences for surviving DTOs. Second, targeting members performing specific tasks had different impacts on DTO resilience: targeting traffickers resulted in the highest rates of DTO disruption, while targeting actors in charge of more redundant tasks (e.g., retailers) had smaller but significant impacts. Third, the model examined the resistance and resilience of DTOs adopting different strategies in the security/efficiency trade-off. Efficient DTOs were more resilient, outperforming secure DTOs in terms of reactions to a single, equal attempt at disruption. Conversely, secure DTOs were more resistant, displaying higher survival rates than efficient DTOs when considering the differentiated frequency and effectiveness of law enforcement interventions on DTOs having different focuses in the security/efficiency trade-off.
Overall, the model demonstrated that law enforcement interventions are often critical events for DTOs, with high rates of both first intention (i.e., DTOs directly disrupted by the intervention) and second intention (i.e., DTOs terminating their activities due to the unsustainability of the intervention’s short-term consequences) culminating in dismantlement. However, surviving DTOs always displayed a high level of resilience, with effective strategies in place to react to threatening events and to continue drug trafficking and dealing.
Peer reviewed Credit and debt market of low-income families
Márton Gosztonyi | Published Tuesday, December 12, 2023 | Last modified Friday, January 19, 2024The purpose of the Credit and debt market of low-income families model is to help the user examine how the financial market of low-income families works.
The model is calibrated based on real-time data which was collected in a small disadvantaged village in Hungary it contains 159 households’ social network and attributes data.
The simulation models the households’ money liquidity, expenses and revenue structures as well as the formal and informal loan institutions based on their network connections. The model forms an intertwined system integrated in the families’ local socioeconomic context through which families handle financial crises and overcome their livelihood challenges from one month to another.
The simulation-based on the abstract model of low-income families’ financial survival system at the bottom of the pyramid, which was described in following the papers:
…
Peer reviewed Theoretical Model of Oak Persistence Under Competition and Herbivory
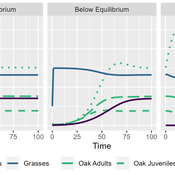
MV Eitzel Solera | Published Tuesday, October 25, 2022This model is intended to support oak tree management by representing the dynamics of oaks in multiple life stages and their competitors and consumers. This is implemented using a differential equation-based theoretical model representing three life stages of oaks: seedlings, juveniles, and adults. It includes the population dynamics of seedlings transitioning to juveniles, juveniles to adults, and adults producing new seedlings, as well as survival rates for each of the stages. It also includes a model of competition for light and water within seedlings and between seedlings and annual grasses. Finally, there is a predation term representing herbivores eating seedlings and grasses, using a Holling Type II (satiating) response with interference for predators and a death rate which depends on the resource extraction rate.
Survival analysis and Population viability analysis of the Northern Bald Ibis
Stephanie Kramer-Schadt Cédric Scherer Viktoriia Radchuk Sinah Drenske Corinna Esterer Ingo Kowarik Johannes Fritz | Published Thursday, August 04, 2022This is the full repository to run the survival analysis (in R) and run the population viability model and its analysis (NetLogo + R) of the Northern Bald Ibis (NBI) presented in the study
On the road to self-sustainability: Reintroduced migratory European Northern Bald Ibises (Geronticus eremita) still need management interventions for population viability
by Sinah Drenske, Viktoriia Radchuk, Cédric Scherer, Corinna Esterer, Ingo Kowarik, Johannes Fritz, Stephanie Kramer-Schadt
…
BEEHAVE Extension: Varroa mite control within Good Beekeeping Practice in Germany
Volker Grimm Jürgen Groeneveld Isabel Schödl | Published Wednesday, May 25, 2022 | Last modified Monday, November 07, 2022The western honey bee Apis mellifera is the most important pollinator in the world. The biggest threat to managed honey bees is the ectoparasitic mite Varroa destructor and the viruses DWV (Deformed Wing Virus) and APV (Acute Paralysis Virus) it transmits. Untreated honey bee colonies are expected to die within one to three years. This led to the development of strategies for beekeepers to control the Varroa mite in honey bee colonies and ensure the health and survival of their bee colonies, so called Good Beekeeping Practice. The aim of the extension of BEEHAVE was to represent the Good Beekeeping Practice of Varroa control in Germany. The relevant measures within the Varroa control strategies are drone brood removal as a Varroa trap and the treatment of bee colonies with organic acaricides (formic and oxalic acid) to kill the mites. This extension improves BEEHAVE and builds a bridge between beekeepers in practice and in the modelling world. It vastly contributes to the future use of BEEHAVE in beekeeping education in Germany.
Retail Competition Agent-based Model
Derek Robinson Jiaxin Zhang | Published Sunday, January 03, 2021 | Last modified Wednesday, November 10, 2021The Retail Competition Agent-based Model (RC-ABM) is designed to simulate the retail competition system in the Region of Waterloo, Ontario, Canada, which which explicitly represents store competition behaviour. Through the RC-ABM, we aim to answer 4 research questions: 1) What is the level of correspondence between market share and revenue acquisition for an agent-based approach compared to a traditional location-allocation-based approach? 2) To what degree can the observed store spatial pattern be reproduced by competition? 3) To what degree are their path dependent patterns of retail success? 4) What is the relationship between retail survival and the endogenous geographic characteristics of stores and consumer expenditures?
Peer reviewed Circular Business Model experimentation: local biodigestion network
Igor Nikolic Kasper Pieter Hendrik Lange Gijsbert Korevaar Paulien Herder | Published Thursday, December 17, 2020 | Last modified Tuesday, June 29, 2021The purpose of the model is to explore the influence of the design of circular business models (CBMs) on CBM viability. The model represents an Industrial Symbiosis Network (ISN) in which a processor uses the organic waste from suppliers to produce biogas and nutrient rich digestate for local reuse. CBM viability is expressed as value captured (e.g., cash flow/tonne waste/agent) and the survival of the network over time (shown in the interface).
In the model, the value captured is calculated relative to the initial state, using incineration costs as a benchmark. Moderating variables are interactions with the waste incinerator and actor behaviour factors. Actors may leave the network when the waste supply for local production is too low, or when personal economic benefits are too low. When the processor decides to leave, the network fails. Theory of planned behaviour can be used to include agent behaviour in the simulations.
Displaying 10 of 26 results survival clear search