About the CoMSES Model Library more info
Our mission is to help computational modelers at all levels engage in the establishment and adoption of community standards and good practices for developing and sharing computational models. Model authors can freely publish their model source code in the Computational Model Library alongside narrative documentation, open science metadata, and other emerging open science norms that facilitate software citation, reproducibility, interoperability, and reuse. Model authors can also request peer review of their computational models to receive a DOI.
All users of models published in the library must cite model authors when they use and benefit from their code.
Please check out our model publishing tutorial and contact us if you have any questions or concerns about publishing your model(s) in the Computational Model Library.
We also maintain a curated database of over 7500 publications of agent-based and individual based models with additional detailed metadata on availability of code and bibliometric information on the landscape of ABM/IBM publications that we welcome you to explore.
Displaying 10 of 35 results MatLab clear
A double-layer network and the contagion mechanism of China’s financial systemic risk
zou | Published Tuesday, August 13, 2019We establish a double-layer network for China’s financial system, consisting of an interbank lending network and a cross-shareholding network. The loss of diffusion in an interbank lending channel independently, a cross-shareholding channel independently and a double-layer contagion channel after one of the financial institutions goes bankrupt with an initial shock are simulated to explore the nonlinear evolution mechanism of financial risk and impact factors of financial systemic risk in China.
Online Collaboration, Competing for Attention
Miles Manning | Published Wednesday, July 19, 2017 | Last modified Thursday, January 24, 2019This is a model of a community of online communities. Using mechanisms such as win-stay, lose-shift, and preferential attachment the model can reproduce similar patterns to those of the Stack Exchange network.
The impact of potential crowd behaviours on emergency evacuation: an evolutionary game theoretic approach
Azhar Mohd Ibrahim | Published Monday, July 30, 2018Crowd dynamics have important applications in evacuation management systems relevant to organizing safer large scale gatherings. For crowd safety, it is very important to study the evolution of potential crowd behaviours by simulating the crowd evacuation process. Planning crowd control tasks by studying the impact of crowd behaviour evolution towards evacuation could mitigate the possibility of crowd disasters. During a typical emergency evacuation scenario, conflict among agents occurs when agents intend to move to the same location as a result of the interaction with their nearest neighbours. The effect of the agent response towards their neighbourhood is vital in order to understand the effect of variation of crowd behaviour on the whole environment. In this work, we model crowd motion subject to exit congestion under uncertainty conditions in a continuous space via computer simulations. We model best-response, risk-seeking, risk-averse and risk-neutral behaviours of agents via certain game theoretic notions. We perform computer simulations with heterogeneous populations in order to study the effect of the evolution of agent behaviours towards egress flow under threat conditions. Our simulation results show the relation between the local crowd pressure and the number of injured agents. We observe that when the proportion of agents in a population of risk-seeking agents is increased, the average crowd pressure, average local density and the number of injured agents increases. Besides that, based on our simulation results, we can infer that crowd disasters could be prevented if the agent population consists entirely of risk-averse and risk-neutral agents despite circumstances that lead to threats.
How does knowledge infrastructure mobilization influence the safe operating space of regulated exploited ecosystems?
Jean-Denis Mathias | Published Tuesday, July 17, 2018Decision-makers often have to act before critical times to avoid the collapse of ecosystems using knowledge \textcolor{red}{that can be incomplete or biased}. Adaptive management may help managers tackle such issues. However, because the knowledge infrastructure required for adaptive management may be mobilized in several ways, we study the quality and the quantity of knowledge provided by this knowledge infrastructure. In order to analyze the influence of mobilized knowledge, we study how the following typology of knowledge and its use may impact the safe operating space of exploited ecosystems: 1) knowledge of the past based on a time series distorted by measurement errors; 2) knowledge of the current systems’ dynamics based on the representativeness of the decision-makers’ mental models of the exploited ecosystem; 3) knowledge of future events based on decision-makers’ likelihood estimates of extreme events based on modeling infrastructure (models and experts to interpret them) they have at their disposal. We consider different adaptive management strategies of a general regulated exploited ecosystem model and we characterize the robustness of these strategies to biased knowledge. Our results show that even with significant mobilized knowledge and optimal strategies, imperfect knowledge may still shrink the safe operating space of the system leading to the collapse of the system. However, and perhaps more interestingly, we also show that in some cases imperfect knowledge may unexpectedly increase the safe operating space by suggesting cautious strategies.
The code enables to calculate the safe operating spaces of different managers in the case of biased and unbiased knowledge.
Social Closure and the Evolution of Cooperation via Indirect Reciprocity
Simone Righi Károly Takács | Published Saturday, June 09, 2018 | Last modified Saturday, June 09, 2018Righi S., Takacs K., Social Closure and the Evolution of Cooperation via Indirect Reciprocity, Resubmitted after Revisions to Scientific Reports
Adaptive model of a consumer advice network
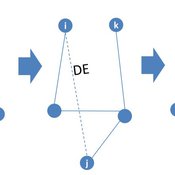
Peng Shao | Published Monday, May 14, 2018In the consumer advice network, users with connections can interact with each other, and the network topology will change during the opinion interaction. When the opinion distance from i to j is greater than the confidence threshold, the two consumers cannot exchange opinions, and the link between them will disconnect with probability DE. Then, a link from node i to node k is established with probability CE and node i learning opinion from node k.
Peter Diamond's Coconut Model (Heterogeneity and Learning)
Sven Banisch Eckehard Olbrich | Published Monday, May 30, 2016Agent-based version of the simple search and barter economy conceived by Peter Diamond in 1982. The model is also known as Coconut Model.
Lewis' Signaling Chains
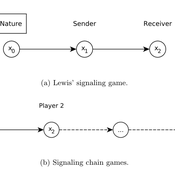
Giorgio Gosti | Published Wednesday, January 14, 2015 | Last modified Friday, April 03, 2015Signaling chains are a special case of Lewis’ signaling games on networks. In a signaling chain, a sender tries to send a single unit of information to a receiver through a chain of players that do not share a common signaling system.
Hedonic and Eudaimonic Well-being Based Reward for Intrinsic Motivated Reinforcement Learning Agents
Yue Gao Shimon Edelman | Published Monday, March 21, 2016The code contains four experiments for well-being based IMRL reward features.
An Agent-Based Model of Collective Action
Hai-Hua Hu | Published Tuesday, August 20, 2013We provide an agent-based model of collective action, informed by Granovetter (1978) and its replication model by Siegel (2009). We use the model to examine the role of ICTs in collective action under different cultural and political contexts.
Displaying 10 of 35 results MatLab clear